For doing this you need a simple Software, The link is given Bellow:
PkySetup
With Piky Basket, you can reduce repetitive tasks when copying/moving files and folders in Windows. Piky Basket allows you to select files/folders in to a "basket" from different locations. Once you are done selecting, you can paste them all at once to the target folders. It also allows you to selectively paste the files to the target folder.
Piky Basket is integrated with Windows Explorer. You do not have to run Piky Basket as a separate program. It can be accessed from the menu which appears by right clicking on any files/folders in Windows Explorer.
If you didn't get it how it work just look at the screen shot Carefully...!! It will Help you out...!!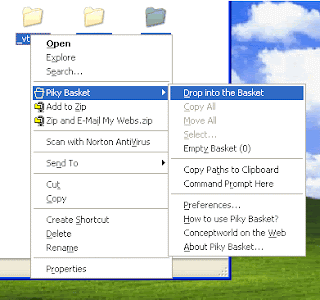
Copying And Droping content into Basket